Vendor: EC-Council
Exam Code: 312-76
Exam Name: EC-Council Disaster Recovery Professional (EDRP)
QUESTION 1
Which of the following roles is responsible for the review and risk analysis of all the contracts on regular basis?
A. The IT Service Continuity Manager
B. The Configuration Manager
C. The Supplier Manager
D. The Service Catalogue Manager
Answer: C
QUESTION 2
Which of the following is established during the Business Impact Analysis by the owner of a process in accepted business continuity planning methodology?
A. Recovery Consistency Objective
B. Recovery Time Objective
C. Recovery Point Objective
D. Recovery Time Actual
Answer: B
QUESTION 3
Which of the following options is an intellectual property right to protect inventions?
A. Snooping
B. Patent
C. Copyright
D. Utility model
Answer: D
QUESTION 4
Pete works as a Network Security Officer for Gentech Inc. He wants to encrypt his network traffic. The specific requirement for the encryption algorithm is that it must be a symmetric key block cipher. Which of the following techniques will he use to fulfill this requirement?
A. AES
B. DES
C. IDEA
D. PGP
Answer: B
QUESTION 5
Which of the following is the simulation of the disaster recovery plans?
A. Walk-through test
B. Full operational test
C. Paper test
D. Preparedness test
Answer: B
QUESTION 6
You work as the project manager for Bluewell Inc. Your project has several risks that will affect several stakeholder requirements. Which project management plan will define who will be
available to share information on the project risks?
A. Communications Management Plan
B. Resource Management Plan
C. Risk Management Plan
D. Stakeholder management strategy
Answer: A
QUESTION 7
Which of the following levels of RAID provides security features that are availability, enhanced performance, and fault tolerance?
A. RAID-10
B. RAID-5
C. RAID-0
D. RAID-1
Answer: A
QUESTION 8
Which of the following backup sites takes the longest recovery time?
A. Cold backup site
B. Hot backup site
C. Warm backup site
D. Mobile backup site
Answer: A
QUESTION 9
Peter works as a Technical Representative in a CSIRT for SecureEnet Inc. His team is called to investigate the computer of an employee, who is suspected for classified data theft. Suspect’s computer runs on Windows operating system. Peter wants to collect data and evidences for further analysis. He knows that in Windows operating system, the data is searched in pre-defined
steps for proper and efficient analysis. Which of the following is the correct order for searching data on a Windows based system?
A. Volatile data, file slack, registry, system state backup, internet traces, file system, memory dumps
B. Volatile data, file slack, internet traces, registry, memory dumps, system state backup, file system
C. Volatile data, file slack, registry, memory dumps, file system, system state backup, internet traces
D. Volatile data, file slack, file system, registry, memory dumps, system state backup, internet traces
Answer: D
QUESTION 10
Which of the following defines the communication link between a Web server and Web applications?
A. IETF
B. Firewall
C. PGP
D. CGI
Answer: D
QUESTION 11
Which of the following plans is documented and organized for emergency response, backup operations, and recovery maintained by an activity as part of its security program that will ensure the availability of critical resources and facilitates the continuity of operations in an emergency situation?
A. Disaster Recovery Plan
B. Continuity Of Operations Plan
C. Business Continuity Plan
D. Contingency Plan
Answer: D
QUESTION 12
Which of the following features of the Cisco MDS 9000 SAN Extension over IP Package help in implementing efficient FCIP-based business-continuity and disaster-recovery solutions?
Each correct answer represents a complete solution. Choose all that apply.
A. FCIP write acceleration
B. IVR
C. FCIP compression
D. SAN extension tuner
Answer: BC
QUESTION 13
Which of the following methods is a means of ensuring that system changes are approved before being implemented, and the implementation is complete and accurate?
A. Configuration identification
B. Configuration control
C. Configuration auditing
D. Documentation control
Answer: D
QUESTION 14
Which of the following roles is responsible for review and risk analysis of all contracts on a regular basis?
A. The IT Service Continuity Manager
B. The Configuration Manager
C. The Supplier Manager
D. The Service Catalogue Manager
Answer: C
QUESTION 15
Which of the following statements about a certification authority (CA) is true?
A. It is a non-profit organization that sets security standards for e-commerce.
B. It is a business-to-consumer (B2C) commerce model that is used for high-volume transactions.
C. It is a trusted third-party organization that issues digital certificates to create digital signatures and public
key pairs.
D. It issues physical certificates that confirm the identity of entities.
Answer: C
QUESTION 16
BS 7799 is an internationally recognized ISM standard that provides high level, conceptual recommendations on enterprise security. BS 7799 is basically divided into three parts. Which of the following statements are true about BS 7799?
Each correct answer represents a complete solution. Choose all that apply.
A. BS 7799 Part 3 was published in 2005, covering risk analysis and management.
B. BS 7799 Part 1 was a standard originally published as BS 7799 by the British Standards Institute (BSI)
in 1995.
C. BS 7799 Part 2 was adopted by ISO as ISO/IEC 27001 in November 2005.
D. BS 7799 Part 1 was adopted by ISO as ISO/IEC 27001 in November 2005.
Answer: ABC
QUESTION 17
An organization monitors the hard disks of its employees’ computers from time to time. Which policy does this pertain to?
A. User password policy
B. Backup policy
C. Privacy policy
D. Network security policy
Answer: C
QUESTION 18
Which of the following disaster recovery tests includes the operations that shut down at the primary site, and are shifted to the recovery site according to the disaster recovery plan?
A. Parallel test
B. Simulation test
C. Full-interruption test
D. Structured walk-through test
Answer: C
QUESTION 19
Fill in the blank with the appropriate phrase.
____________ privilege escalation is the process of attempting to access sources with a higher access, such as a user account trying to access admin privileges.
Answer: Vertical
QUESTION 20
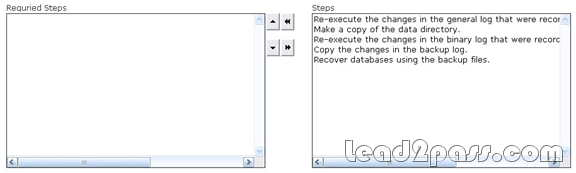
Choose the steps involved in the general disaster recovery procedure.
QUESTION 21
Which of the following backup sites is the best way for rapid recovery if you do not need the full recovery temporarily?
A. Hot backup site
B. Cold backup site
C. Mobile backup site
D. Warm backup site
Answer: C
If you want to pass EC-Council 312-76 successfully, donot missing to read latest lead2pass EC-Council 312-76 practice exams.
If you can master all lead2pass questions you will able to pass 100% guaranteed.